- AWS KMS is a managed service that is integrated with various other AWS Services. You can use it in your applications to create, store and control encryption keys to encrypt your data. KMS allows you to gain more control for access to the data that you encrypt. KMS assures 9999% durability of.
- Setting up the AWS KMS. Contributors Download PDF of this page. If you want to use Amazon encryption with Cloud Volumes ONTAP, then you need to set up the AWS Key Management Service (KMS). Ensure that an active Customer Master Key (CMK) exists.
- An AWS KMS CMK for each secret Each secret is associated with an AWS managed or customer managed customer master key (CMK). Customer managed CMKs allow authorized users to control access to the CMK through policies and grants, manage.
- AWS Key Management Store (KMS) is a managed service that enables you to easily encrypt your data. AWS KMS provides a highly available key storage, management, and auditing solution for you to encrypt data within your own applications and control the encryption of stored data across AWS services.
Easily create and control the keys used to encrypt or digitally sign your data
AWS KMS supports symmetric and asymmetric CMKs. A symmetric CMK represents a 256-bit key that is used for encryption and decryption. An asymmetric CMK represents an RSA key pair that is used for encryption and decryption or signing and verification (but not both), or an elliptic curve (ECC) key pair that is used for signing and verification.
AWS Key Management Service (KMS) makes it easy for you to create and manage cryptographic keys and control their use across a wide range of AWS services and in your applications. AWS KMS is a secure and resilient service that uses hardware security modules that have been validated under FIPS 140-2, or are in the process of being validated, to protect your keys. AWS KMS is integrated with AWS CloudTrail to provide you with logs of all key usage to help meet your regulatory and compliance needs.

Try AWS Key Management Service
AWS Free Tier includes 20,000 free AWS Key Management Service requests each month.

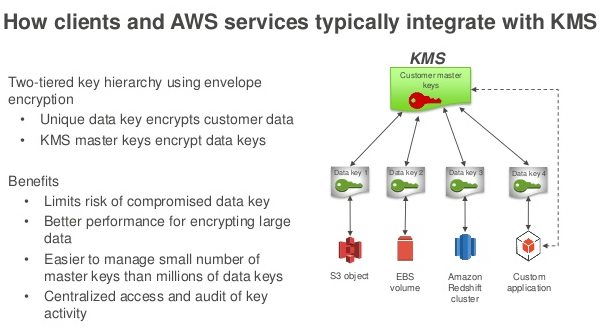
Benefits
Aws Kms Developer Guide
Fully managed
You control access to your encrypted data by defining permissions to use keys while AWS KMS enforces your permissions and handles the durability and physical security of your keys.
Centralized key management
AWS KMS presents a single control point to manage keys and define policies consistently across integrated AWS services and your own applications. You can easily create, import, rotate, delete, and manage permissions on keys from the AWS Management Console or by using the AWS SDK or CLI.
Learn more >>
Manage encryption for AWS services
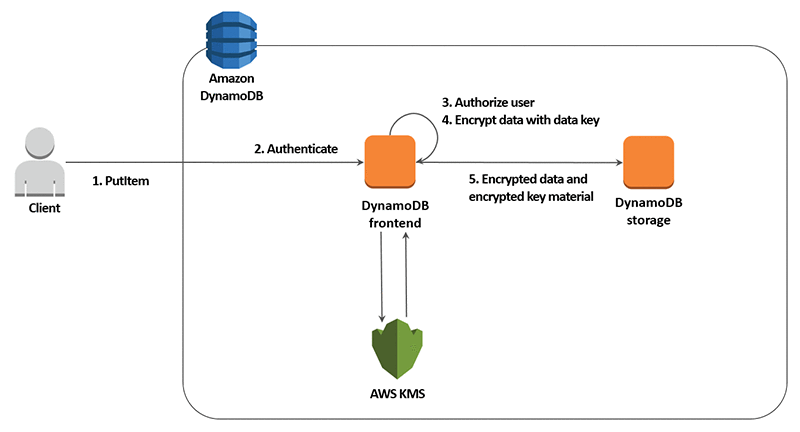
AWS KMS is integrated with AWS services to simplify using your keys to encrypt data across your AWS workloads. You choose the level of access control that you need, including the ability to share encrypted resources between accounts and services. KMS logs all use of keys to AWS CloudTrail to give you an independent view of who accessed your encrypted data, including AWS services using them on your behalf.
Educating westover mother. Learn more >>
Encrypt data in your applications
Aws Kms Encrypt
AWS KMS is integrated with the AWS Encryption SDK to enable you to used KMS-protected data encryption keys to encrypt locally within your applications. Using simple APIs you can also build encryption and key management into your own applications wherever they run.
Learn more >>
Digitally sign data
AWS KMS enables you to perform digital signing operations using asymmetric key pairs to ensure the integrity of your data. Recipients of digitally signed data can verify the signatures whether they have an AWS account or not.
Aws Kms Decrypt
Learn more >>
Schneider_electric driver download.
Low cost
There is no commitment and no upfront charges to use AWS KMS. You only pay US $1/month to store any key that you create. AWS managed keys that are created on your behalf by AWS services are free to store. You are charged per-request when you use or manage your keys beyond the free tier.
Learn more >>
Google Chrome is a fast, free web browser. Before you download, you can check if Chrome supports your operating system and you have all the other system requirements. Get more done with the new Google Chrome. A more simple, secure, and faster web browser than ever, with Google’s smarts built-in. Chrome web browser 2020.
Secure
AWS KMS uses hardware security modules (HSMs) that have been validated under FIPS 140-2, or are in the process of being validated, to generate and protect keys. Your keys are only used inside these devices and can never leave them unencrypted. KMS keys are never shared outside the AWS region in which they were created.
Learn more >>
Compliance
The security and quality controls in AWS KMS have been certified under multiple compliance schemes to simplify your own compliance obligations. AWS KMS provides the option to store your keys in single-tenant HSMs in AWS CloudHSM instances that you control.
Learn more >>
Built-in auditing
AWS KMS is integrated with AWS CloudTrail to record all API requests, including key management actions and usage of your keys. Logging API requests helps you manage risk, meet compliance requirements and conduct forensic analysis.
Learn more >>
Blog posts & articles
Read about AWS Key Management Service security, compliance, and availability.
Learn moreInstantly get access to the AWS Free Tier.
Sign upGet started building with AWS Key Management Service in the AWS Console.
Aws Where Is Kms Used
Sign in